Mikrotik OpenVPN Server
The purpose of this post is to describe, step by step, my attempt to set up an OpenVPN server on a Mikrotik RouterBOARD 750 and create a working tunnel from an outside machine (AWS EC2 Windows Server 2008 R2) to this OpenVPN server so that an SMB server on the local network can be accessed from said outside machine. The following diagram gives an overview of the setup:
I am going to decribe how to:
- generate certificates to be used with OpenVPN
- set up OpenVPN server on Mikrotik router
- set up a tunnel with OpenVPN client on Windows
- setting up and connecting to an EC2 Windows instance
- setting up a Samba Server
- only supports TCP mode, UDP is not supported
- username/password pair is also required even though certificates are being used for authentication
Generate certificates to be used with OpenVPN
root@inhouse-debian:~# apt-get install openvpn root@inhouse-debian:~# mkdir ovpn-cert root@inhouse-debian:~# cd ovpn-cert/ root@inhouse-debian:~/ovpn-cert# cp -r /usr/share/doc/openvpn/examples/easy-rsa/2.0/* . root@inhouse-debian:~/ovpn-cert# emacs varsIn the file
vars I set the following values:
export KEY_COUNTRY="FI" export KEY_PROVINCE="Etela-Suomi" export KEY_CITY="Kotka" export KEY_ORG="Async.fi" export KEY_EMAIL="joni.kahara@async.fi" export KEY_CN="kahara.dyndns.org" export KEY_NAME="kahara.dyndns.org" export KEY_OU="kahara.dyndns.org"If I have understood correctly, of these only CN (Common Name) is obligatory. I may be wrong. Anyway, continuing:
root@inhouse-debian:~/ovpn-cert# source vars root@inhouse-debian:~/ovpn-cert# ./clean-all root@inhouse-debian:~/ovpn-cert# ./build-ca root@inhouse-debian:~/ovpn-cert# ./build-key-server kahara.dyndns.org root@inhouse-debian:~/ovpn-cert# openssl rsa -in keys/kahara.dyndns.org.key -out keys/kahara.dyndns.org.pem root@inhouse-debian:~/ovpn-cert# ./build-key ec2 root@inhouse-debian:~/ovpn-cert# apt-get install ncftp root@inhouse-debian:~/ovpn-cert# ncftpput -u admin 192.168.1.1 / keys/kahara.dyndns.org.crt keys/kahara.dyndns.org.pem keys/ca.crt
Set up OpenVPN server on Mikrotik router
All the stuff here can also be made through Mikrotik's admin interface; textual form without screen shots is used just to keep thing terse.root@inhouse-debian:~/ovpn-cert# ssh admin@192.168.1.1 [admin@MikroTik] > /certificate [admin@MikroTik] /certificate> import file=kahara.dyndns.org.crt [admin@MikroTik] /certificate> import file=kahara.dyndns.org.pem [admin@MikroTik] /certificate> import file=ca.crt [admin@MikroTik] /certificate> decrypt [admin@MikroTik] /certificate> .. [admin@MikroTik] > /interface bridge add name=ovpn-bridge [admin@MikroTik] > /interface bridge port add interface=ether2-master-local bridge=ovpn-bridge [admin@MikroTik] > /ip address add address=192.168.1.64/24 interface=ovpn-bridge [admin@MikroTik] > /ip pool add name=ovpn-pool ranges=192.168.1.65-192.168.1.99 [admin@MikroTik] > /ppp profile add bridge=ovpn-bridge name=ovpn-profile remote-address=ovpn-pool [admin@MikroTik] > /ppp secret add service=ovpn local-address=192.168.1.64 name=user1 password=pass1 profile=ovpn-profile [admin@MikroTik] > /interface ovpn-server server set auth=sha1,md5 certificate=cert1 cipher=blowfish128,aes128,aes192,aes256 default-profile=ovpn-profile enabled=yes keepalive-timeout=disabled max-mtu=1500 mode=ethernet netmask=24 port=1194 require-client-certificate=yes [admin@MikroTik] > /ip firewall filter add action=accept chain=input disabled=no protocol=tcp dst-port=1194 [admin@MikroTik] > /ip firewall filter move 5 destination=1That last step moves the new rule to the front of the chain; numbers ("5", "1") will likely be something else on your configuration. Firewall rule listing can be printed with the following command:
[admin@MikroTik] > /ip firewall filter print
Setup up a tunnel with OpenVPN client on Windows
After installing OpenVPN, create a config file for it. Here it's called "kahara.dyndns.org.ovpn":client dev tap proto tcp remote kahara.dyndns.org 1194 resolv-retry infinite nobind persist-key persist-tun ca ca.crt cert ec2.crt key ec2.key verb 3 pull auth-user-pass userpass.txtAlso, create a file called "userpass.txt" and put the following to it:
user1 pass1Of course in an IRL situation one should use a real password. Make sure you copied the .crt and .key files over to the Windows machine, after which you can run OpenVPN client with:
PS C:\Users\Administrator\Desktop> openvpn.exe .\kahara.dyndns.org.ovpnAnd here we have an EC2 client connected to a local SMB resource over the tunnel:
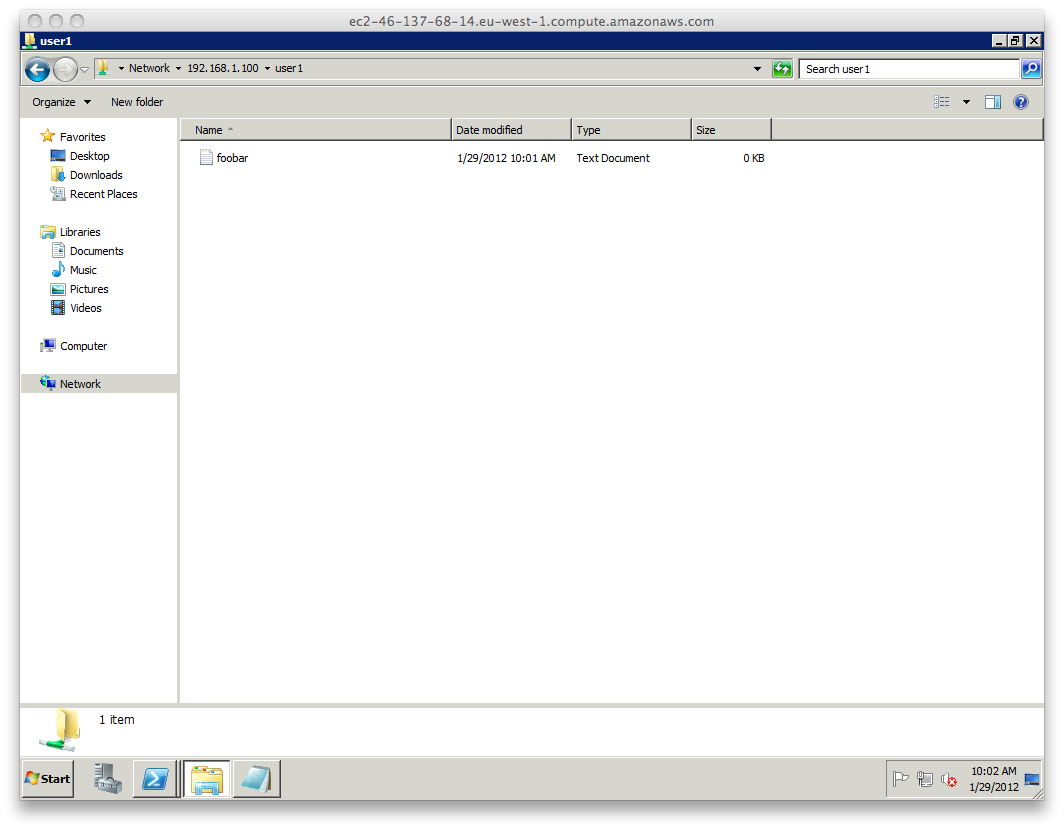
Categorised as: experimental
